The cybersecurity landscape is increasingly hostile, especially for small to medium-sized businesses (SMBs). Facing advanced persistent threats (APTs) and ransomware syndicates with limited budgets and staff, SMBs need a force multiplier. This post summarizes the key insights from our book, AI-Enabled Blue Teams, on how to build a resilient, AI-powered security stack without breaking the bank.
The Case for AI in Defense
As explored in Chapter 1, the traditional perimeter is dead. With 70% of organizations struggling to hire security talent, manual triage is no longer sustainable. Artificial Intelligence (AI) and Machine Learning (ML) are not just buzzwords—they are essential tools for survival. By automating routine tasks like log parsing and initial triage, AI frees up human analysts to focus on high-value decision-making.
A Modular, Open-Source Architecture
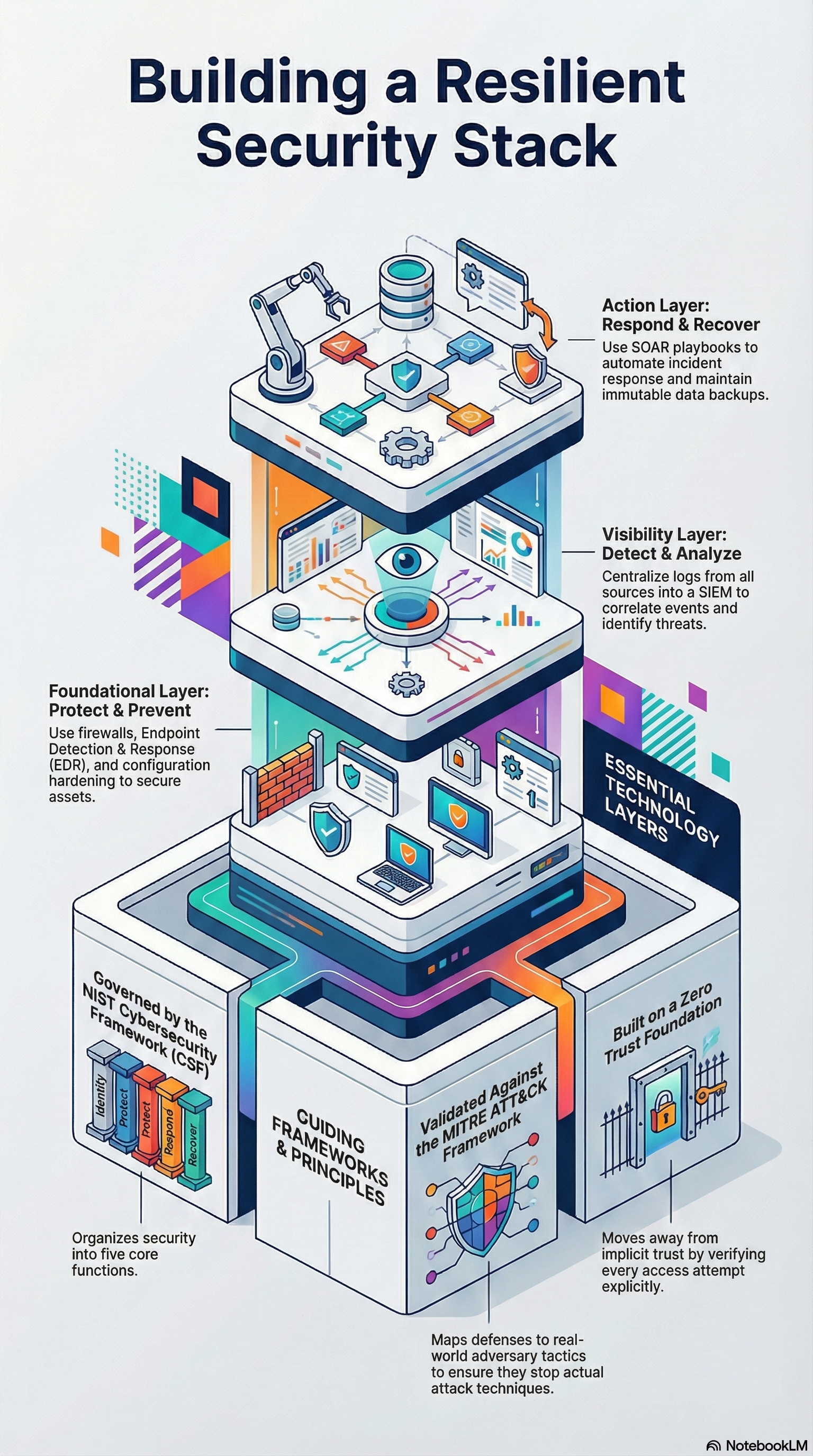
You don’t need a million-dollar budget to build an enterprise-grade SOC. Chapter 5 outlines a powerful, modular architecture built entirely on open-source tools:
- Ingestion & SIEM: Elastic Stack (Beats, Logstash, Elasticsearch, Kibana) serves as the central nervous system for log aggregation and visualization.
- Threat Intelligence: OpenCTI manages global threat data, allowing you to enrich local alerts with context about threat actors and malware families.
- Endpoint Security: Wazuh provides host-based intrusion detection (HIDS) and active response capabilities to block threats at the device level.
- AI Brain: Locally hosted Llama-2 models summarize complex logs, while FAISS vector databases enable semantic search to find “nearest neighbor” threats from historical data.
AI-Driven Detection and Response
The core of this modern stack is the pipeline described in Chapter 3. Raw logs are not just stored; they are transformed into vector embeddings using Sentence-Transformers. This allows for anomaly detection that goes beyond simple signature matching, catching “unknown unknowns” by identifying deviations from normal behavior.
For response, we move beyond static playbooks. Chapter 4 introduces Reinforcement Learning (RL) agents trained with Stable-Baselines3. These agents learn to mitigate threats dynamically, balancing the need for speed (mean time to containment) with the risk of disrupting business operations (false positives).
Human-AI Collaboration
Ultimately, technology is there to augment the human analyst, creating a “Centaur” model of defense (Chapter 6). A robust Governance framework (Chapter 7) ensures that these AI systems remain transparent, fair, and compliant with regulations like GDPR and NIST.
Deep Dives and Discussions
To help you get started on this journey, we have compiled a series of deep-dive audio discussions covering the technical implementation and strategic mandates associated with this stack:
Building Enterprise Security with Open Source Tools: A comprehensive walkthrough of the architecture and integration strategies.
Enforcing Mandatory Security Configurations: How to use Wazuh and Ansible to ensure your baseline security controls are immutable.
NIST, MITRE, DMARC, and FIDO2 Mandates: Understanding the regulatory landscape and how this stack helps you achieve compliance.
By leveraging these open-source tools and AI methodologies, small teams can punch above their weight, building a defense that is not only resilient but continuously evolving to meet the threats of tomorrow.